By Adrien Cherqui
Translation: Anton Stzepourginski
Passage au crible n°89
 Source: Wikimedia
Source: Wikimedia
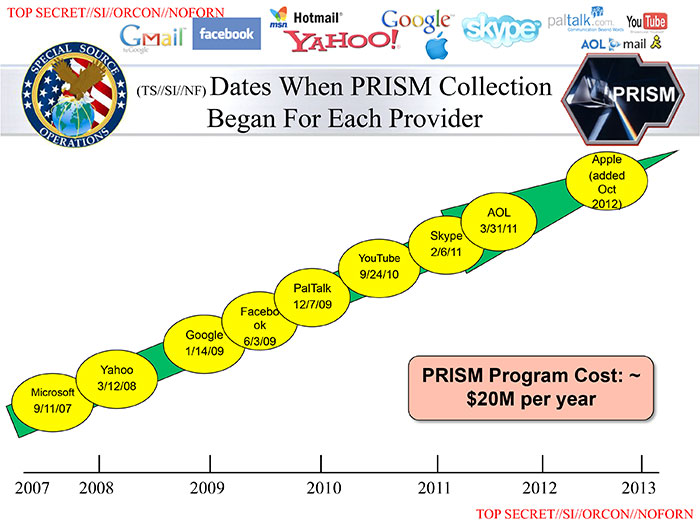
The American program PRISM (Planning Tool for Resource Integration, Synchronization, and Management) which collects Internet users’ personal data has been making the news over the last few days everywhere in the world. Several major companies such as Google, Facebook, Microsoft, Yahoo, AOL or the telephone operator Verizon provide the US security agencies full access to their databases. In other words, US Intelligence gathers phone calls, emails, photos, videos and any other types of data.
> Historical background
> Theoretical framework
> Analysis
> References
On the 12th of March 2013, the US Congress stated that General Keith Alexander – Chief of the Central Security Service, Director of the NSA (National Security Agency) and Commander of the United States Cyber Command – had been authorized to set up 13 teams of programmers and IT experts in order to protect American networks against foreign attacks. For the first time, the Obama Administration was publicly recognizing to plan and set about such a defense strategy. A few weeks later, Pentagon officials said they had discovered that Chinese hackers had entered the American systems and accessed 30 defense technologies, 40 military equipment programs – such as the Patriot missile –, the AEGIS naval antimissile command, fighter planes (F35, F/A-18) and the Black Hawk helicopter. Edward Snowden – former CIA analyst which has been living in exile in Hong-Kong since the 20th of May 2013 – told the media that the NSA had hacked several Chinese computers and Hong-Kong University’s IXP (Internet Exchange Point), a physical infrastructure that allows Internet service operators to exchange internet traffic between their respective networks. Edward Snowden also revealed the existence of PRISM since 2007 that allow collecting data from several sources, such as the Internet.
1. Configuration. According to Norbert Elias, a configuration refers to the individuals and their interdependent relationships. That notion overcomes the classic dichotomy commonly established between the individual and the society by the social sciences, and all its paradoxes. Therefore, this term refers to mutually dependent relations that are complex and dynamic.
2. Hegemony. Due to multiple arrangements with transnational companies, the United States demonstrate their digital hegemony. They have the power to impose their own rules and agreements to other actors in the global arena. They establish their supremacy over the Internet by protecting and reinforcing the monopoly and the continued dominance of major US groups in the fields of cloud services and new technologies.
New means of communication and interaction have been exposed by the development of NTIC (New Information and Communication Technology) and the expansion of the Internet network. According to Marcel Mauss, technology – or the study of techniques – constitutes an important part of sociology. Therefore, in order to improve understanding of rapid and massive changes, technologies’ growth and impact have to be taken into consideration. Today, ideas, identities and practices are transnationalized through the existence of online meeting places, social networks (Facebook, Twitter) and Internet forums.
The notion of risk constitutes a policy challenge. Indeed, there are technique evolutions that can jeopardize social groups (Ulrich Bech). Based on this perspective, the United States legitimate their security policies in accordance with Max Weber’s concept of monopoly of the legitimate use of force. Today, individuals have the right to express themselves freely on the Internet, and this freedom has become a challenge for companies and States. Surveillance programs such as ECHELON – a global communication interception system ruled by Intelligence agencies of Canada, United States, Great Britain, Australia and New-Zealand – or PRISM are not new. Indeed, PRISM works in the same way as Bentham’s panopticon in the 18th century: it gathers personal data that pass through Internet providers’ networks. American intelligence agencies are at the core of this framework and they can gather a large number of confidential information. From times to times, private and public actors were already working together to check and collect data from Google or Yahoo members. PRISM represents a straight continuation of such partnership policy between private firms and public service. It creates mutual dependent relationships and fosters cooperation. This decompartmentalization between the private and public spheres also underlines the process of globalization and strengthens behavior traffic between heterogeneous actors. Such cooperation and interaction between national authorities and other actors not only created interdependency but also reshaped international order. That kind of partnership is not trivial because it takes part in strengthening American hegemony over the Internet. Indeed, private firms have been providing the United States with essential resources in order to establish their hegemony. Through a hegemonic coalition (Gramsci), the country now has a privileged access to the Silicon Valley and its database. That process allows national authorities to initiate a global policy of gathering personal data in a clandestine manner. Such predation has become possible because of the growing monopolistic use of dematerialized products provided by these American companies.
It reveals how weak individual and public freedoms are in a country which intends to know as much as possible on everyone. American Civil Liberties Union – one of the main associations fighting for civil liberties and against the collection of personal data – initiated legal action against PRISM. There were violent reactions which showed bonds of solidarity between organizations and individuals who where supposed to have no direct link. Therefore, a configuration of players is being set up. On the one hand, large private groups act hand in hand with the US government, and on the other hand individuals use services controlled by PRISM.
This increased surveillance of the Internet underlines a twofold phenomenon: reinforced espionage of politics units at the micro and macro levels. Whistleblower Edward Snowden said that computers and infrastructures were hacked in China (such as the IXP in Hong Kong). In the end, American supremacy over the Internet is based on the relationship between the United States and the private sector. Their hegemony reveals that national authorities established contacts with large transnational firms, and that essential resources have been granted to the United States. America now plays a major role in this field, and it is still developing.
Arquilla John, Ronfeldt David, « Cyberwar is Coming! », Comparative Strategy, 12 (2), 1993, p. 141-165.
Assange Julian, « L’avancée des technologies de l’information annonce la fin de la vie privée », Le Monde, 7 juin 2013, disponible à la page : http://www.lemonde.fr/idees/article/2013/06/07/le-fardeau-du-geek-blanc_3426437_3232.html
Mauss Marcel, Techniques, technologies et civilisation, Paris, PUF, 2012.
Mazzetti Mark, Sanger David E., « Security Leader Says U.S. Would Retaliate Against Cyberattacks», The New York Times, 12 mars 2013, disponible à la page: http://www.nytimes.com/2013/03/13/us/intelligence-official-warns-congress-that-cyberattacks-pose-threat-to-us.html?_r=2&
Rosenau James N., Sign J. P. (Ed.), Informations Technologies and Global Politics, The Changing Scope of Power and Governance, Albany, State University of New York Press, 2002.
Rosenau James N., Turbulence in World Politics: a Theory of Change and Continuity, Princeton, Princeton University Press, 1990.
Samaan Jean-Loup, « Mythes et réalités des cyberguerres », Politique étrangère, 4, 2008, p. 829-841.




